Understanding the Cyber Kill Chain
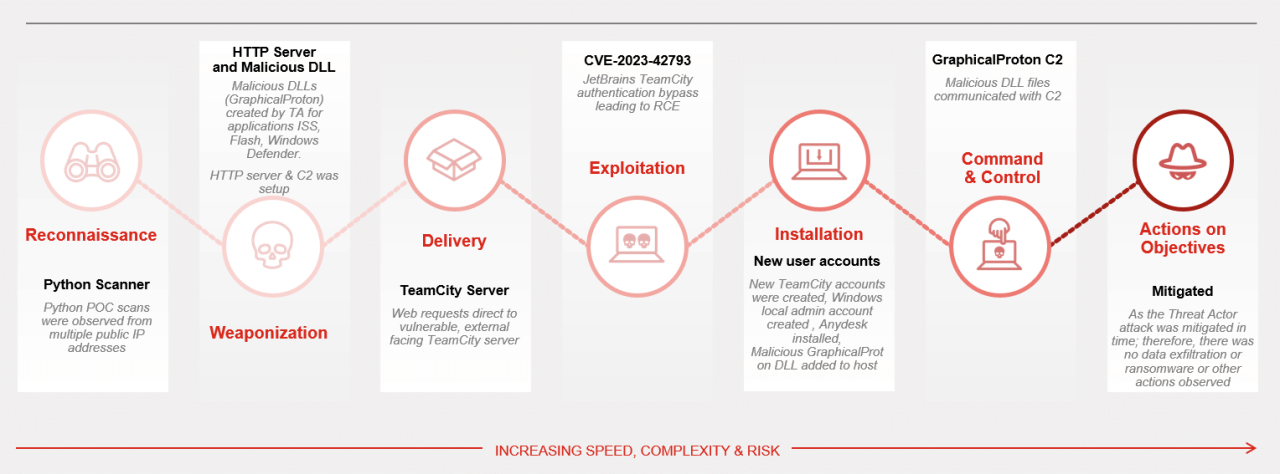
The Cyber Kill Chain consists of seven sequential stages that attackers typically follow:
- Reconnaissance – Gathering information about targets and identifying vulnerabilities
- Weaponization – Creating malicious payloads and exploit kits
- Delivery – Transmitting malicious content to targets via email, web, or other vectors
- Exploitation – Taking advantage of vulnerabilities to execute malicious code
- Installation – Establishing persistent presence through malware installation
- Command & Control (C2) – Setting up communication channels with compromised systems
- Actions on Objectives – Achieving the attacker’s ultimate goals (data theft, disruption, etc.)
Fortinet Security Fabric Overview
The Fortinet Security Fabric provides a comprehensive, integrated security platform that interconnects discrete security solutions into an integrated whole to detect, monitor, block, and remediate attacks across the entire attack surface. It delivers broad protection and visibility into every network segment and device, whether hardware, virtual, or cloud-based.
Comprehensive Defense Mapping with Cyber Kill Chain
Stage 1: Reconnaissance
Attack Vector: Attackers gather information about targets, identify vulnerabilities, scan networks, and collect employee data from social media.
Fortinet Defense Products:
- FortiGate NGFW – Provides network scanning protection and monitors for suspicious reconnaissance activities
- FortiNAC – Delivers comprehensive network visibility and device discovery to detect unauthorized scanning
- FortiAnalyzer – Performs log analysis and correlates threat intelligence to identify reconnaissance patterns
- FortiGuard Labs – Supplies global threat intelligence on emerging reconnaissance techniques
Stage 2: Weaponization
Attack Vector: Attackers create malware, exploit kits, and weaponized payloads tailored to identified vulnerabilities.
Fortinet Defense Products:
- FortiSandbox – Analyzes suspicious files and URLs to identify weaponized content using AI-powered behavioral analysis
- FortiGuard Labs – Provides real-time threat intelligence and malware signatures
- FortiAnalyzer – Correlates threat data to identify weaponization patterns and emerging threats
Stage 3: Delivery
Attack Vector: Malicious payloads are delivered via email attachments, infected websites, USB drives, or network exploits.
Fortinet Defense Products:
- FortiGate NGFW – Blocks malicious traffic through IPS, web filtering, and application control
- FortiMail – Provides comprehensive email security against spam, phishing, and malware
- FortiWeb – Protects web applications from attacks targeting known and unknown exploits
- FortiClient – Delivers endpoint protection with real-time threat detection
- FortiProxy – Offers secure web gateway capabilities with SSL inspection and content filtering
- FortiAP – Provides secure wireless access with integrated threat protection
Stage 4: Exploitation
Attack Vector: Vulnerabilities are exploited to gain unauthorized access, execute malicious code, and escalate privileges.
Fortinet Defense Products:
- FortiGate NGFW – Prevents exploitation through advanced IPS and application control
- FortiWeb – Defends against web application exploits including OWASP Top 10 threats
- FortiSandbox – Detects zero-day exploits through behavioral analysis
- FortiClient – Provides endpoint detection and response capabilities
- FortiNAC – Controls network access and enforces security policies
- FortiSwitch – Enables network segmentation and access control at the switching layer
- FortiAP – Secures wireless access points against exploitation attempts
Stage 5: Installation
Attack Vector: Persistent malware, backdoors, and rootkits are installed to maintain access and establish a foothold.
Fortinet Defense Products:
- FortiClient – Provides anti-malware protection and endpoint detection
- FortiEDR – Offers advanced endpoint detection and response with behavioral analysis
- FortiSandbox – Analyzes malware installation behaviors and techniques
- FortiAnalyzer – Correlates logs to detect installation activities and persistence mechanisms
Stage 6: Command & Control (C2)
Attack Vector: Remote communication channels are established with command servers for data exfiltration.
Fortinet Defense Products:
- FortiGate NGFW – Inspects traffic and blocks C2 communications through advanced threat detection
- FortiProxy – Analyzes web traffic for suspicious C2 communications
- FortiAnalyzer – Monitors network communications for C2 patterns
- FortiMail – Detects email-based C2 channels
- FortiEDR – Identifies and blocks endpoint C2 activities
- DNS Security – Blocks malicious domain communications
Stage 7: Actions on Objectives
Attack Vector: Attackers achieve final objectives including data theft, system disruption, lateral movement, and ransomware deployment.
Fortinet Defense Products:
- FortiAnalyzer – Provides forensic analysis and incident investigation capabilities
- FortiGate NGFW – Implements data loss prevention and network isolation
- FortiNAC – Performs network isolation and quarantine of compromised devices
- FortiProxy – Prevents data exfiltration through DLP capabilities
- FortiEDR – Enables rapid incident response and threat containment
- FortiSwitch – Supports network segmentation to limit lateral movement
Security Fabric Integration Benefits
The power of the Fortinet Security Fabric lies in its unified management and automated threat response capabilities. Key integration benefits include:
Coordinated Threat Intelligence
All Security Fabric components share policy, threat intelligence, and application flow information in real-time. This collaborative approach expands network visibility and enables fast threat detection across the entire attack surface.
Automated Response
When threats are detected at any stage, the Security Fabric can automatically isolate affected devices, partition network segments, update rules, push new policies, and remove malware.
Centralized Management
FortiManager provides centralized configuration and policy management across all Security Fabric components, while FortiAnalyzer delivers unified logging, analysis, and reporting.
Comprehensive Coverage
The Security Fabric architecture ensures complete visibility and protection across endpoints, networks, applications, and cloud environments, creating multiple layers of defense against each kill chain stage.






