The Cyber Kill Chain, developed by Lockheed Martin, provides a framework for understanding the stages of cyberattacks, from initial reconnaissance to achieving the attacker’s final objectives. It consists of the following seven sequential stages:
SOC maturity model (5 steps: Initial → Optimized)
The pictured maturity staircase shows how security capabilities evolve across People, Process, and Technology from ad-hoc operations to a continuously improving, optimized SOC.
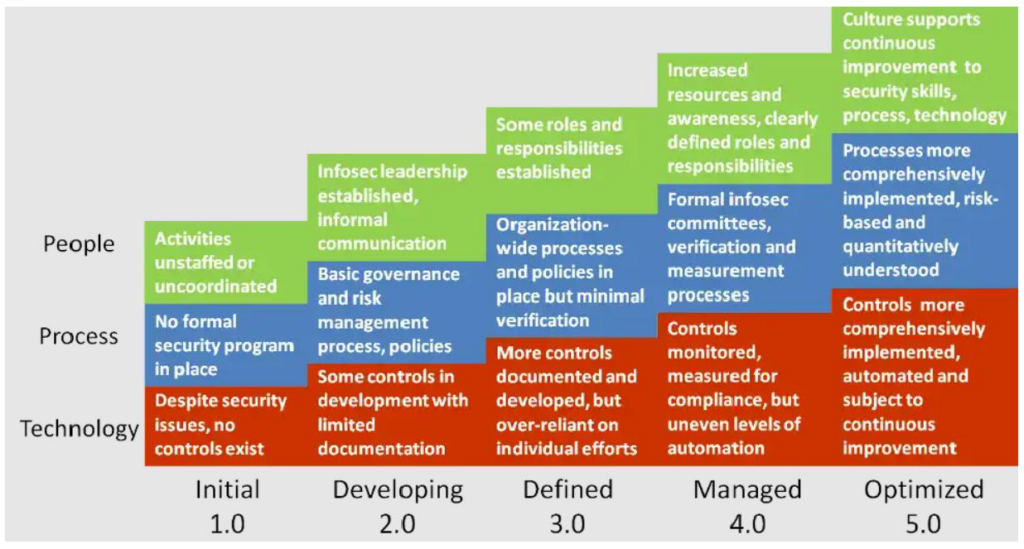
1. Initial (1.0)
At this stage, security work is mostly reactive and fragmented.
- People: Activities are unstaffed or uncoordinated—security depends on a few individuals.
- Process: No formal security program exists; actions are inconsistent.
- Technology: Even though issues occur, meaningful controls are not in place.
2. Developing (2.0)
The organization starts building structure, but it’s still early.
- People: An infosec leader emerges and communication begins (often informal).
- Process: Basic governance and risk processes appear—some policies start forming.
- Technology: Controls begin development, but documentation and standardization are limited.
3. Defined (3.0)
Security becomes organization-wide, but measurement is still weak.
- People: Some roles and responsibilities are formally established.
- Process: Organization-wide policies/processes exist, but verification is minimal.
- Technology: More controls are deployed and documented, though outcomes may rely heavily on individual effort.
4. Managed (4.0)
Security operations become measurable and consistently executed.
- People: Resources and awareness increase; roles/responsibilities are clearly defined.
- Process: Formal committees and verification/measurement processes are introduced.
- Technology: Controls are monitored and measured for compliance, but automation may be uneven.
5. Optimized (5.0)
Security becomes a continuous improvement engine, not a periodic project.
- Technology: Controls are broadly implemented, automated, and continuously improved.
- People: Culture supports continuous improvement in skills, process, and technology.
- Process: Processes are comprehensive, risk-based, and quantitatively understood.
The 3 big challenges security teams face (and what they mean)
The Venn diagram highlights three recurring SOC pain points that modern security architectures try to solve together.
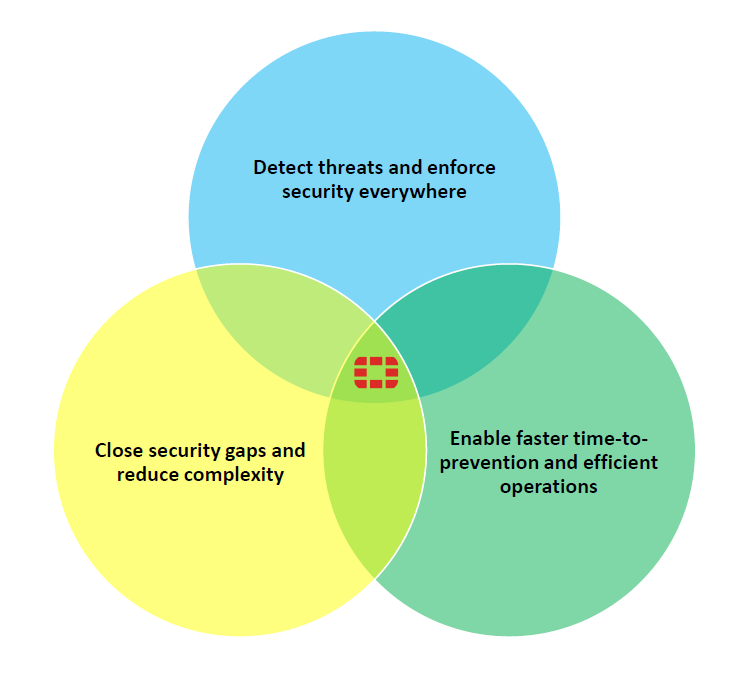
1) Detect threats and enforce security everywhere
Organizations struggle because threats appear across endpoints, cloud, apps, identities, email, and network, often outside one tool’s visibility. The real challenge is consistent detection and policy enforcement across all these environments without blind spots.
2) Close security gaps and reduce complexity
Many SOCs run too many disconnected tools. That creates gaps (things falling between tools) and complexity (duplicate alerts, inconsistent policies, integration headaches). Reducing complexity means fewer silos, cleaner integrations, and fewer “unknown unknowns.”
3) Enable faster time-to-prevention and efficient operations
Even when detections exist, response can be slow due to manual triage, noisy alerts, and limited staff. Faster time-to-prevention means shortening the cycle from “signal” → “decision” → “action,” while keeping workload sustainable.
Products from the fabric to achieve level 5 SOC maturity:
FortiSIEM
FortiSIEM is positioned as a central visibility + analytics layer for SOC operations, focused on real-time monitoring, correlation, and scalable log management.
- Comprehensive visibility: It provides real-time visibility across network devices, applications, and endpoints—so the SOC can monitor activity end-to-end rather than in isolated tool views.
- Advanced threat detection: By correlating events and applying analytics, it helps surface threats and vulnerabilities that aren’t obvious in single logs.
- Automated incident response: It streamlines incident handling so the SOC reduces reaction time (for example, by auto-generating incidents from correlated detections and routing them to the right workflows).
- Centralized log management: It consolidates logs from multiple sources, improving investigations, reporting, and compliance evidence collection.
- Scalability: It is designed to scale as the organization’s devices, users, and log volumes grow.
Accelerators for detection and operational efficiency: 3000+ out-of-the-box rules, a UEBA (User & Entity Behavior Analytics) engine, and FortiAI automation
FortiSOAR
FortiSOAR is presented as the automation/orchestration layer that reduces manual SOC work and standardizes response.
- Streamlined workflows: It automates and orchestrates incident response flows—reducing repetitive steps and speeding up response timelines.
- Collaboration: It improves SOC teamwork by embedding communication and documentation into the response process (so incidents don’t live in scattered chats and tickets).
- Playbooks: It uses predefined and customizable playbooks to standardize response—so actions are repeatable, auditable, and less dependent on individual experience.
- Threat intelligence integration: It connects to multiple TI sources to enrich alerts and improve context during triage.
- Efficiency: By automating repetitive tasks, it helps analysts focus on higher-value investigations.
Operational scale features: 800+ pre-built playbooks, 600+ vendor integrations, no-code playbook creation, AI-driven operations, and SLA/queue tracking, all aimed at running a more predictable and measurable SOC.
FortiEDR
FortiEDR is described as an endpoint protection platform focused on continuous monitoring, behavior-based detection, and fast remediation—while staying lightweight for users.
- Real-time protection: Continuous monitoring and protection against endpoint threats—so suspicious activity is detected as it happens, not after the fact.
- Behavioral analysis: Detects sophisticated attacks by identifying abnormal behaviors (useful against fileless attacks and techniques that evade signature-only tools).
- Automated remediation: Automatically contains/remediates threats to reduce disruption and speed up recovery.
- Integration: Works with other security tools (including other Fortinet components and third parties) to support a unified security posture.
- Minimal impact: A lightweight agent approach is emphasized—important because heavy endpoint tools can slow systems and reduce user adoption.
Legacy system support, compatibility across older Windows workstation and Windows Server versions, useful for environments where older systems still exist.
FortiRecon
FortiRecon is positioned as a “digital risk” and external threat intelligence capability—helping SOC teams detect and prioritize risks earlier, including risks outside the perimeter.
- Enhanced visibility: Provides a broader view of internal and external risks, helping teams detect threats early (including brand-related and exposed-asset risks).
- Proactive risk management: Helps identify and prioritize risks so teams can act before issues escalate into incidents.
- Improved incident response: Delivers actionable intelligence that reduces both response time and overall cost of mitigation.
- Brand protection: Focuses on identifying and addressing cyber risks that could damage trust and reputation (e.g., impersonation, exposed credentials, misuse).
- Comprehensive threat intelligence: Leverages FortiGuard Labs intelligence to better understand threat actors and tactics.
- Centralized management: Offers a single platform to manage digital risk, simplifying operations.
It integrates with SIEM and SOAR for enrichment and correlation, reduces MTTR with organization-tailored threat intelligence, and maps detections to the MITRE ATT&CK framework to better describe adversary tactics/techniques (TTPs).
Conclusion
With Fortinet’s integrated security approach, SOC maturity becomes a clear, step-by-step progression, not a “big bang” overhaul. Instead of trying to solve everything at once, you build capability layer by layer: visibility first, then consistency, then speed through automation, until the SOC operates like a well-run engine with measurable outcomes and continuous improvement.
The real unlock isn’t just better tools. It’s how the SOC runs. Defining frameworks, SOPs, and runbooks at each maturity stage creates a repeatable operating model: triage becomes predictable, escalations become faster, and incident response becomes consistent across analysts and shifts. By the time you reach Stage 5 (Optimized), the SOC is streamlined, auditable, and continuously tuned to reduce noise and improve response.
But security isn’t a destination, it’s a journey. The practical way forward:
1) Baseline where you are today
Start with a thorough assessment of your current security posture – coverage, visibility gaps, detection quality, response readiness, and tool integration. The goal is a clear maturity baseline and a prioritized roadmap of improvements.
2) Operationalize the SOC playbook, stage by stage
At every step, build tangible assets, not just documentation: SOPs for daily operations, runbooks for common incidents (phishing, credential compromise, ransomware), escalation paths, and metrics like MTTD/MTTR to track progress.
3) Strengthen the posture beyond the SOC
As maturity improves, evaluate complementary capabilities that reduce exposure and close gaps, identity hardening, cloud security, vulnerability management, data protection, and external risk monitoring, so prevention and response evolve together.
That’s how you move from reactive firefighting to a SOC that’s structured, efficient, and built to keep improving as threats and business needs change.






